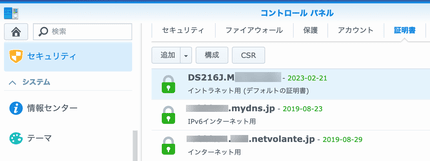
「XXXXXXXX.mydns.jp(IPv6)」と「XXXXXXXX.YYY.netvolante.jp(IPv4)」の証明書有効期限(2019/6/14 JST)が近づき30日以内となりDS-216Jコントロールパネル・セキュリティ・証明書の有効期限日が赤色となった。いつ更新されるのか確認していたが、5月25日にIPv6の証明書が更新され、IPv4の証明書は、更新されていなかった。IPv6用証明書の更新が失敗したメールが届き、コントロールパネルから手動更新した記憶があったため、ログを確認してみた。
Let's Encryptの証明書再取得は、「/usr/syno/sbin/syno-letsencrypt」で実行される
自動更新は毎週設定されているが何故か定期的で無いようだ。weekly random?
/var/log/synocrond-execute.log(syno-letsencryptの実行結果ログ)
/var/log/nginx/access.log(Let's Encryptからのhttpサーバ確認結果ログ)
/var/log/synoservice.log(httpサーバ設定再読込ログ)
これらのログを時系列に並べてみる
前回(2019年3月16日)の自動更新時ログ
「syno-letsencrypt」が実行され、更新対象の証明書が存在すると「更新処理」が始まる。
「ブラウザで動くLet's Encryptクライアントを作ってみた」が参考になる。「syno-letsencrypt」は、Let's Encryptからの「HTTP-01」認証を待つ。「port 80」の解放が必須。「port 80」が閉じていて認証に失敗すると、「syno-letsencrypt」は、「DNS-01」認証に切替える。「redirect 80 -> 443」でも問題なく「HTTP-01」認証が行われる。下記ログでは、IPv6用証明書が先に自動更新対象となり「HTTP-01」認証が行われ、ログに残らないが証明書の更新がされ、「httpサーバのreload」で更新されていた。続いてIPv4用証明書が更新された。「httpサーバ設定のreload」の実行タイミングがIPv4サーバへの「HTTP-01」認証より前に実行されることに疑問。その後、「weekly random」に自動更新チェックが行われるが、「有効期限30日前」までは、更新処理が行われない。
2019年3月16日 03:12:06 JSTに生成されたサーバ証明書は、
有効期限: 2019年6月14日 03:12:06 JST
30日前: 2019年5月14日 03:12:06 JST
証明書発行時のタイムスタンプが1時間ズレているのが気になる。。。
有効期限30日前以降で「syno-letsencrypt」が実行されたのは、2019年5月25日で下記の結果となった。Let's Encryptからの「HTTP-01」認証前後で「synoservice.log」に「httpサーバ設定の再読込」ログは、記録されていなかった。IPv4サーバの「HTTP-01」認証後に「Unexpect httpcode」のエラー発生記録が残っていた。エラー発生が「httpサーバ設定の再読込」を停止させたのか、システムアップデートで仕様が変更になったのか不明。
次の自動更新実行を待ってみた。
4日後に実行されたがエラー内容「no valid domain name」が異なる。
手動で「syno-letsencrypt」をデバッグ実行し確認してみた。
「ブラウザで動くLet's Encryptクライアントを作ってみた」を参考にしながら分析してみたがエラー原因は「?」であった。
「invalid anti-replay nonce ltldAhF-SePLQsPxnwoGJ8b6dIUXSczmDhrwiVmOhuw」であるが、「directory」操作の直後の「new-authz」なので「direcorty」操作結果時の「Reply-nonce(下記青文字)」。しかし、この「Reply-nonce」が「invalid」と言われてはどうにもならない。。。
日を置いて再度手動で実行してみたが結果は、「no valid domain name」
「-vv」だと結果が長いので「-v」で実行してみた
?「new-authz」が成功し、「new-certs」を実行している。。。。しかし「/usr/syno/etc/certificate/_archive/aaaaaa/cert.pem」に変化が無かった。
気を取り直して再度「-vv」で実行してみたら「save to file」された。。。
「new-authz」で認知している証明書の有効期限が「2019-06-24T11:01:35Z」と発行された証明書の有効期限「Jun 13 18:12:06 2019 GMT」と異なっている。これが原因かもしれない。
更新された証明書は、下記の通り
2019年5月31日 17:51:29 JST から
2019年8月29日 17:51:29 JST まで
タイムスタンプが1時間ズレているのは変わらず
次回の更新は、「2019年7月30日(火) 17:51:29 JST」以降なので、忘れなければ、デバッグ実行して証明書と「new-authz」の有効期限を確認することにする。

Let's Encryptの証明書再取得は、「/usr/syno/sbin/syno-letsencrypt」で実行される
----
sh-4.3# /usr/syno/sbin/syno-letsencrypt --help
Copyright (c) 2003-2019 Synology Inc. All rights reserved.
syno-letsencrypt <command> [<args>]
new-cert
-d [domains] Domain name to be registed. (required)
-m [mail] Email address for contact. (required)
-s [server] Let's encrypt directory URL. (optional)
-c [certid] Certificat Id. (optional)
renew-all
revoke
-c [cert-path] revoke a certificat. (required)
For all command, you can add the following arguments for debug.
-v Show debug message.
-vv Show more debug message.
------- /usr/syno/etc/synocron.d/syno-letsencrypt.conf
[
{
"cmd" : "/usr/syno/sbin/syno-letsencrypt renew-all",
"name" : "syno-letsencrypt - renew",
"period" : "weekly",
"user" : "root"
}
]
---/var/log/nginx/access.log(Let's Encryptからのhttpサーバ確認結果ログ)
/var/log/synoservice.log(httpサーバ設定再読込ログ)
これらのログを時系列に並べてみる
前回(2019年3月16日)の自動更新時ログ
「syno-letsencrypt」が実行され、更新対象の証明書が存在すると「更新処理」が始まる。
「ブラウザで動くLet's Encryptクライアントを作ってみた」が参考になる。「syno-letsencrypt」は、Let's Encryptからの「HTTP-01」認証を待つ。「port 80」の解放が必須。「port 80」が閉じていて認証に失敗すると、「syno-letsencrypt」は、「DNS-01」認証に切替える。「redirect 80 -> 443」でも問題なく「HTTP-01」認証が行われる。下記ログでは、IPv6用証明書が先に自動更新対象となり「HTTP-01」認証が行われ、ログに残らないが証明書の更新がされ、「httpサーバのreload」で更新されていた。続いてIPv4用証明書が更新された。「httpサーバ設定のreload」の実行タイミングがIPv4サーバへの「HTTP-01」認証より前に実行されることに疑問。その後、「weekly random」に自動更新チェックが行われるが、「有効期限30日前」までは、更新処理が行われない。
--synocrond-execute.log
03-16 04:12:00 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
-- synoservice.log
2019-03-16T04:12:01+09:00 ds216j builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew: service_reload.c:20 synoservice: reload [nginx].
2019-03-16T04:12:05+09:00 ds216j builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew: service_reload.c:46 synoservice: finish reload [nginx].
--access.log(IPv6)
2600:3000:2710:200::1d - - [16/Mar/2019:04:12:07 +0900] "GET /.well-known/acme-challenge/QplO5L0dXgR9H_pjE3fWqpqZZMSN8PDX3q7wdZ8hheI HTTP/1.1" 301 178 "-" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)" "-"
2600:3000:2710:200::1d - - [16/Mar/2019:04:12:07 +0900] "https" "GET /.well-known/acme-challenge/QplO5L0dXgR9H_pjE3fWqpqZZMSN8PDX3q7wdZ8hheI HTTP/1.1" 200 87 "http://XXXXXXXX.mydns.jp/.well-known/acme-challenge/QplO5L0dXgR9H_pjE3fWqpqZZMSN8PDX3q7wdZ8hheI" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)" "-"
-- synoservice.log
2019-03-16T04:12:09+09:00 ds216j builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew: service_reload.c:20 synoservice: reload [nginx].
2019-03-16T04:12:11+09:00 ds216j builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew: service_reload.c:46 synoservice: finish reload [nginx].
2019-03-16T04:12:16+09:00 ds216j builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew: service_reload.c:20 synoservice: reload [nginx].
2019-03-16T04:12:18+09:00 ds216j builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew: service_reload.c:46 synoservice: finish reload [nginx].
--access.log(IPv4)
66.133.109.36 - - [16/Mar/2019:04:12:20 +0900] "http" "GET /.well-known/acme-challenge/6CAasz2BB2P0EfGj18MZE-1uzYVqyZbbrInQNfvVPUk HTTP/1.1" 301 178 "-" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)" "-"
66.133.109.36 - - [16/Mar/2019:04:12:21 +0900] "https" "GET /.well-known/acme-challenge/6CAasz2BB2P0EfGj18MZE-1uzYVqyZbbrInQNfvVPUk HTTP/1.1" 200 87 "http://XXXXXXXX.YYY.netvolante.jp/.well-known/acme-challenge/6CAasz2BB2P0EfGj18MZE-1uzYVqyZbbrInQNfvVPUk" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)" "-"--synocrond-execute.log
03-24 10:13:31 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
03-30 23:22:47 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
04-03 14:30:51 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
04-08 20:48:08 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
04-18 06:38:49 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
04-28 01:44:00 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
05-04 23:56:55 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
05-09 08:28:02 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
05-13 07:04:13 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
----有効期限: 2019年6月14日 03:12:06 JST
30日前: 2019年5月14日 03:12:06 JST
証明書発行時のタイムスタンプが1時間ズレているのが気になる。。。
----
sh-4.3# openssl x509 -text -noout -in /usr/syno/etc/certificate/_archive/aaaaaa/cert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
03:e7:15:a0:0b:c5:ce:31:1b:ef:3e:a8:87:98:61:95:de:2d
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, O=Let's Encrypt, CN=Let's Encrypt Authority X3
Validity
Not Before: Mar 15 18:12:06 2019 GMT
Not After : Jun 13 18:12:06 2019 GMT
Subject: CN=XXXXXXXX.YYY.netvolante.jp
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
**:**:........
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
F3:9D:D2:CF:E6:A5:13:DC:39:DC:CE:02:4E:7A:C3:5F:6D:CE:61:88
X509v3 Authority Key Identifier:
keyid:A8:4A:6A:63:04:7D:DD:BA:E6:D1:39:B7:A6:45:65:EF:F3:A8:EC:A1
Authority Information Access:
OCSP - URI:http://ocsp.int-x3.letsencrypt.org
CA Issuers - URI:http://cert.int-x3.letsencrypt.org/
X509v3 Subject Alternative Name:
DNS:XXXXXXXX.YYY.netvolante.jp
X509v3 Certificate Policies:
Policy: 2.23.140.1.2.1
Policy: 1.3.6.1.4.1.44947.1.1.1
CPS: http://cps.letsencrypt.org
CT Precertificate SCTs:
Signed Certificate Timestamp:
Version : v1(0)
Log ID : **:**:........
Timestamp : Mar 15 19:12:06.281 2019 GMT
Extensions: none
Signature : ecdsa-with-SHA256
**:**:........
Signed Certificate Timestamp:
Version : v1(0)
Log ID : **:**:........
Timestamp : Mar 15 19:12:06.308 2019 GMT
Extensions: none
Signature : ecdsa-with-SHA256
Signature Algorithm: sha256WithRSAEncryption
**:**:........----synocrond-execute.log
05-25 20:03:02 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
----access.log(IPv6)
2600:3000:2710:200::1d - - [25/May/2019:20:03:04 +0900] "GET /.well-known/acme-challenge/x0z5LSNhqyI1CmrBny8TDIvxIpWcgzivsqmjRg5BJes HTTP/1.1" 301 162 "-" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)" "-"
2600:3000:2710:200::1d - - [25/May/2019:20:03:05 +0900] "https" "GET /.well-known/acme-challenge/x0z5LSNhqyI1CmrBny8TDIvxIpWcgzivsqmjRg5BJes HTTP/1.1" 200 87 "http://XXXXXXXX.mydns.jp/.well-known/acme-challenge/x0z5LSNhqyI1CmrBny8TDIvxIpWcgzivsqmjRg5BJes" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)" "-"
----access.log(IPv4)
66.133.109.36 - - [25/May/2019:20:03:11 +0900] "http" "GET /.well-known/acme-challenge/AlaIVSed-2BgUfxNdZqk3xHiTQXEryk1iRquDgz-iBc HTTP/1.1" 301 162 "-" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)" "-"
66.133.109.36 - - [25/May/2019:20:03:11 +0900] "https" "GET /.well-known/acme-challenge/AlaIVSed-2BgUfxNdZqk3xHiTQXEryk1iRquDgz-iBc HTTP/1.1" 200 87 "http://XXXXXXXX.YYY.netvolante.jp/.well-known/acme-challenge/AlaIVSed-2BgUfxNdZqk3xHiTQXEryk1iRquDgz-iBc" "Mozilla/5.0 (compatible; Let's Encrypt validation server; +https://www.letsencrypt.org)" "-"
----/var/log/messages.log
2019-05-25T20:03:17+09:00 ds216j builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew: syno-letsencrypt.cpp:351 Failed to renew /usr/syno/etc/certificate/_archive/aaaaaa. {"error":200,"file":"client.cpp","msg":"new-cert: Unexpect httpcode. (new-cert)"}
----次の自動更新実行を待ってみた。
4日後に実行されたがエラー内容「no valid domain name」が異なる。
----synocrond-execute.log
05-29 03:30:20 running job: builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew with command: /usr/syno/sbin/syno-letsencrypt renew-all as user root
----/var/log/messages.log
2019-05-29T03:30:21+09:00 ds216j builtin-dyn-syno-letsencrypt-syno-letsencrypt - renew: syno-letsencrypt.cpp:351 Failed to renew /usr/syno/etc/certificate/_archive/aaaaaa. {"error":102,"file":"client.cpp","msg":"no valid domain name"}
----手動で「syno-letsencrypt」をデバッグ実行し確認してみた。
----/var/log/bash_history.log
2019-05-30T15:09:17+09:00 ds216j sh: HISTORY: PID=20397 UID=0 /usr/syno/sbin/syno-letsencrypt renew-all -vv
----synocrond-execute.log
2019-05-30T15:09:18+09:00 ds216j syno-letsencrypt: syno-letsencrypt.cpp:351 Failed to renew /usr/syno/etc/certificate/_archive/aaaaaa. {"error":102,"file":"client.cpp","msg":"no valid domain name"}
----「ブラウザで動くLet's Encryptクライアントを作ってみた」を参考にしながら分析してみたがエラー原因は「?」であった。
「invalid anti-replay nonce ltldAhF-SePLQsPxnwoGJ8b6dIUXSczmDhrwiVmOhuw」であるが、「directory」操作の直後の「new-authz」なので「direcorty」操作結果時の「Reply-nonce(下記青文字)」。しかし、この「Reply-nonce」が「invalid」と言われてはどうにもならない。。。
**********************************
sh-4.3# /usr/syno/sbin/syno-letsencrypt renew-all -vv
DEBUG: Issuer name of certificate. [Let's Encrypt]->[/usr/syno/etc/certificate/_archive/bbbbbb/cert.pem]
DEBUG: cert is not expired. [/usr/syno/etc/certificate/_archive/bbbbbb]
DEBUG: Issuer name of certificate. [Let's Encrypt]->[/usr/syno/etc/certificate/_archive/aaaaaa/cert.pem]
DEBUG: start to renew [/usr/syno/etc/certificate/_archive/aaaaaa].
DEBUG: setup acme url https://acme-v01.api.letsencrypt.org/directory
DEBUG: szUserAgent: [synology_armada38x_ds216j DSM6.2-24922 (DDNS)]
DEBUG: GET Request: https://acme-v01.api.letsencrypt.org/directory
DEBUG: Curl Reply: [200] Header: [HTTP/1.1 200 OK
Server: nginx
Content-Type: application/json
Content-Length: 658
Replay-Nonce: ltldAhF-SePLQsPxnwoGJ8b6dIUXSczmDhrwiVmOhuw
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
Expires: Thu, 30 May 2019 06:07:36 GMT
Cache-Control: max-age=0, no-cache, no-store
Pragma: no-cache
Date: Thu, 30 May 2019 06:07:36 GMT
Connection: keep-alive
] Body: [{
"key-change": "https://acme-v01.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"terms-of-service": "https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf",
"website": "https://letsencrypt.org"
},
"new-authz": "https://acme-v01.api.letsencrypt.org/acme/new-authz",
"new-cert": "https://acme-v01.api.letsencrypt.org/acme/new-cert",
"new-reg": "https://acme-v01.api.letsencrypt.org/acme/new-reg",
"puJR66VWsYI": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417",
"revoke-cert": "https://acme-v01.api.letsencrypt.org/acme/revoke-cert"
}]
DEBUG: strat to do new-authz for XXXXXXXX.YYY.netvolante.jp
DEBUG: ==> start new authz.
DEBUG: new authz: do new-authz.
DEBUG: Post JWS Request: https://acme-v01.api.letsencrypt.org/acme/new-authz
DEBUG: Post JWS value: {
"identifier" : {
"type" : "dns",
"value" : "XXXXXXXX.YYY.netvolante.jp"
},
"resource" : "new-authz"
}
DEBUG: szUserAgent: [synology_armada38x_ds216j DSM6.2-24922 (DDNS)]
DEBUG: Post Request: https://acme-v01.api.letsencrypt.org/acme/new-authz
DEBUG: Post value: {
"header" : {
"alg" : "RS256",
"jwk" : {
"e" : "AQAB",
"kty" : "RSA",
"n" : "m8m---6Nw"
}
},
"payload" : "eyJ---n0K",
"protected" : "eyJ---fQo",
"signature" : "fME---6Kg"
}
DEBUG: Curl Reply: [400] Header: [HTTP/1.1 400 Bad Request
Server: nginx
Content-Type: application/problem+json
Content-Length: 149
Boulder-Requester: 25089748
Replay-Nonce: yla9y2w2mtE1TS5e_yRMWPHkDKoWxDvFXGxbaIqNlM8
Expires: Thu, 30 May 2019 06:07:36 GMT
Cache-Control: max-age=0, no-cache, no-store
Pragma: no-cache
Date: Thu, 30 May 2019 06:07:36 GMT
Connection: close
] Body: [{
"type": "urn:acme:error:badNonce",
"detail": "JWS has invalid anti-replay nonce ltldAhF-SePLQsPxnwoGJ8b6dIUXSczmDhrwiVmOhuw",
"status": 400
}]
DEBUG: Not synology DDNS.
DEBUG: DNS challenge failed, reason: {"error":108,"file":"challenge.cpp","msg":"Not synology DDNS."}
DEBUG: Normal challenge failed, reason: {"error":102,"file":"client.cpp","msg":"no valid domain name"}
**********************************日を置いて再度手動で実行してみたが結果は、「no valid domain name」
----
2019-05-31T14:50:55+09:00 ds216j sh: HISTORY: PID=2652 UID=0 /usr/syno/sbin/syno-letsencrypt renew-all -vv
2019-05-31T14:50:56+09:00 ds216j syno-letsencrypt: syno-letsencrypt.cpp:351 Failed to renew /usr/syno/etc/certificate/_archive/aaaaaa. {"error":102,"file":"client.cpp","msg":"no valid domain name"}
----
2019-05-31T18:31:41+09:00 ds216j sh: HISTORY: PID=9960 UID=0 /usr/syno/sbin/syno-letsencrypt renew-all -vv
2019-05-31T18:31:41+09:00 ds216j syno-letsencrypt: syno-letsencrypt.cpp:351 Failed to renew /usr/syno/etc/certificate/_archive/aaaaaa. {"error":102,"file":"client.cpp","msg":"no valid domain name"}
----「-vv」だと結果が長いので「-v」で実行してみた
----
2019-05-31T18:37:34+09:00 ds216j sh: HISTORY: PID=9960 UID=0 /usr/syno/sbin/syno-letsencrypt renew-all -v
2019-05-31T18:37:37+09:00 ds216j syno-letsencrypt: syno-letsencrypt.cpp:351 Failed to renew /usr/syno/etc/certificate/_archive/aaaaaa. {"error":200,"file":"client.cpp","msg":"new-cert: Unexpect httpcode. (new-cert)"}
----?「new-authz」が成功し、「new-certs」を実行している。。。。しかし「/usr/syno/etc/certificate/_archive/aaaaaa/cert.pem」に変化が無かった。
**********************************
sh-4.3# /usr/syno/sbin/syno-letsencrypt renew-all -v
DEBUG: Issuer name of certificate. [Let's Encrypt]->[/usr/syno/etc/certificate/_archive/bbbbbb/cert.pem]
DEBUG: cert is not expired. [/usr/syno/etc/certificate/_archive/bbbbbb]
DEBUG: Issuer name of certificate. [Let's Encrypt]->[/usr/syno/etc/certificate/_archive/aaaaaa/cert.pem]
DEBUG: start to renew [/usr/syno/etc/certificate/_archive/aaaaaa].
DEBUG: setup acme url https://acme-v01.api.letsencrypt.org/directory
DEBUG: GET Request: https://acme-v01.api.letsencrypt.org/directory
DEBUG: strat to do new-authz for XXXXXXXX.YYY.netvolante.jp
DEBUG: ==> start new authz.
DEBUG: new authz: do new-authz.
DEBUG: Post JWS Request: https://acme-v01.api.letsencrypt.org/acme/new-authz
DEBUG: Post Request: https://acme-v01.api.letsencrypt.org/acme/new-authz
DEBUG: new authz: setup challenge env.
DEBUG: ==> finish new-authz
DEBUG: finish to do new-authz for XXXXXXXX.YYY.netvolante.jp
DEBUG: ==> start new-cert.
DEBUG: generate csr & private key
DEBUG: get new-cert
DEBUG: Post JWS Request: https://acme-v01.api.letsencrypt.org/acme/new-cert
DEBUG: Post Request: https://acme-v01.api.letsencrypt.org/acme/new-cer
**********************************気を取り直して再度「-vv」で実行してみたら「save to file」された。。。
「new-authz」で認知している証明書の有効期限が「2019-06-24T11:01:35Z」と発行された証明書の有効期限「Jun 13 18:12:06 2019 GMT」と異なっている。これが原因かもしれない。
**********************************
sh-4.3# /usr/syno/sbin/syno-letsencrypt renew-all -vv
DEBUG: Issuer name of certificate. [Let's Encrypt]->[/usr/syno/etc/certificate/_archive/bbbbbb/cert.pem]
DEBUG: cert is not expired. [/usr/syno/etc/certificate/_archive/bbbbbb]
DEBUG: Issuer name of certificate. [Let's Encrypt]->[/usr/syno/etc/certificate/_archive/aaaaaa/cert.pem]
DEBUG: start to renew [/usr/syno/etc/certificate/_archive/aaaaaa].
DEBUG: setup acme url https://acme-v01.api.letsencrypt.org/directory
DEBUG: szUserAgent: [synology_armada38x_ds216j DSM6.2-24922 (DDNS)]
DEBUG: GET Request: https://acme-v01.api.letsencrypt.org/directory
DEBUG: Curl Reply: [200] Header: [HTTP/1.1 200 OK
Server: nginx
Content-Type: application/json
Content-Length: 658
Replay-Nonce: IGTmrzH5p5p6rKrOFhNgW_-DoGW-1I4M754lZao-TFI
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
Expires: Fri, 31 May 2019 09:51:23 GMT
Cache-Control: max-age=0, no-cache, no-store
Pragma: no-cache
Date: Fri, 31 May 2019 09:51:23 GMT
Connection: keep-alive
] Body: [{
"key-change": "https://acme-v01.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"terms-of-service": "https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf",
"website": "https://letsencrypt.org"
},
"new-authz": "https://acme-v01.api.letsencrypt.org/acme/new-authz",
"new-cert": "https://acme-v01.api.letsencrypt.org/acme/new-cert",
"new-reg": "https://acme-v01.api.letsencrypt.org/acme/new-reg",
"revoke-cert": "https://acme-v01.api.letsencrypt.org/acme/revoke-cert",
"sf-ffwWC004": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417"
}]
DEBUG: strat to do new-authz for XXXXXXXX.YYY.netvolante.jp
DEBUG: ==> start new authz.
DEBUG: new authz: do new-authz.
DEBUG: Post JWS Request: https://acme-v01.api.letsencrypt.org/acme/new-authz
DEBUG: Post JWS value: {
"identifier" : {
"type" : "dns",
"value" : "XXXXXXXX.YYY.netvolante.jp"
},
"resource" : "new-authz"
}
DEBUG: szUserAgent: [synology_armada38x_ds216j DSM6.2-24922 (DDNS)]
DEBUG: Post Request: https://acme-v01.api.letsencrypt.org/acme/new-authz
DEBUG: Post value: {
"header" : {
"alg" : "RS256",
"jwk" : {
"e" : "AQAB",
"kty" : "RSA",
"n" : "m8m----6Nw"
}
},
"payload" : "eyJ----n0K",
"protected" : "eyJ----fQo",
"signature" : "I-6----19g"
}
DEBUG: Curl Reply: [201] Header: [HTTP/1.1 201 Created
Server: nginx
Content-Type: application/json
Content-Length: 1716
Boulder-Requester: 25089748
Link: ;rel="next"
Location: https://acme-v01.api.letsencrypt.org/acme/authz/PCjGD1iNViYKAHptF4sW4GC2n73bNQNLjeX8Zp7s4fY
Replay-Nonce: LfQjDyHRz5mZfvnFAfCrkZXVp6YBt86soVPhSf8bS08
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
Expires: Fri, 31 May 2019 09:51:23 GMT
Cache-Control: max-age=0, no-cache, no-store
Pragma: no-cache
Date: Fri, 31 May 2019 09:51:23 GMT
Connection: keep-alive
] Body: [{
"identifier": {
"type": "dns",
"value": "XXXXXXXX.YYY.netvolante.jp"
},
"status": "valid",
"expires": "2019-06-24T11:01:35Z",
"challenges": [
{
"type": "tls-alpn-01",
"status": "pending",
"uri": "https://acme-v01.api.letsencrypt.org/acme/challenge/PCjGD1iNViYKAHptF4sW4GC2n73bNQNLjeX8Zp7s4fY/16261719515",
"token": "wWDW2qTAsRD7yqQGqG4xyvy4RdEE3tj0MJUo4SnJWW8"
},
{
"type": "dns-01",
"status": "pending",
"uri": "https://acme-v01.api.letsencrypt.org/acme/challenge/PCjGD1iNViYKAHptF4sW4GC2n73bNQNLjeX8Zp7s4fY/16261719516",
"token": "dYqN6Ks1X9f17esyRqw9MDb-oEY9DTO0A9zF0XpPC5o"
},
{
"type": "http-01",
"status": "valid",
"uri": "https://acme-v01.api.letsencrypt.org/acme/challenge/PCjGD1iNViYKAHptF4sW4GC2n73bNQNLjeX8Zp7s4fY/16261719517",
"token": "AlaIVSed-2BgUfxNdZqk3xHiTQXEryk1iRquDgz-iBc",
"validationRecord": [
{
"url": "http://XXXXXXXX.YYY.netvolante.jp/.well-known/acme-challenge/AlaIVSed-2BgUfxNdZqk3xHiTQXEryk1iRquDgz-iBc",
"hostname": "XXXXXXXX.YYY.netvolante.jp",
"port": "80",
"addressesResolved": [
"220.109.14.ZZZ"
],
"addressUsed": "220.109.14.ZZZ"
},
{
"url": "https://XXXXXXXX.YYY.netvolante.jp/.well-known/acme-challenge/AlaIVSed-2BgUfxNdZqk3xHiTQXEryk1iRquDgz-iBc",
"hostname": "XXXXXXXX.YYY.netvolante.jp",
"port": "443",
"addressesResolved": [
"220.109.14.ZZZ"
],
"addressUsed": "220.109.14.ZZZ"
}
]
}
],
"combinations": [
[
0
],
[
1
],
[
2
]
]
}]
DEBUG: new authz: setup challenge env.
DEBUG: ==> finish new-authz
DEBUG: finish to do new-authz for XXXXXXXX.YYY.netvolante.jp
DEBUG: ==> start new-cert.
DEBUG: generate csr & private key
DEBUG: ======= Private Key ========
DEBUG: -----BEGIN RSA PRIVATE KEY-----
MII----t8Ag==
-----END RSA PRIVATE KEY-----
DEBUG: =========== CSR ============
DEBUG: -----BEGIN CERTIFICATE REQUEST-----
MII----oEd
-----END CERTIFICATE REQUEST-----
DEBUG: get new-cert
DEBUG: Post JWS Request: https://acme-v01.api.letsencrypt.org/acme/new-cert
DEBUG: Post JWS value: {
"csr" : "MII----oEd",
"resource" : "new-cert"
}
DEBUG: szUserAgent: [synology_armada38x_ds216j DSM6.2-24922 (DDNS)]
DEBUG: Post Request: https://acme-v01.api.letsencrypt.org/acme/new-cert
DEBUG: Post value: {
"header" : {
"alg" : "RS256",
"jwk" : {
"e" : "AQAB",
"kty" : "RSA",
"n" : "m8m----6Nw"
}
},
"payload" : "eyJ----9Cg",
"protected" : "eyJ----fQo",
"signature" : "Myx----adw"
}
DEBUG: Curl Reply: [201] Header: [HTTP/1.1 100 Continue
Expires: Fri, 31 May 2019 09:51:29 GMT
Cache-Control: max-age=0, no-cache, no-store
Pragma: no-cache
HTTP/1.1 201 Created
Server: nginx
Content-Type: application/pkix-cert
Content-Length: 1391
Boulder-Requester: 25089748
Link: ;rel="up"
Location: https://acme-v01.api.letsencrypt.org/acme/cert/0326c913416cf8b2b24471b835b71230fd27
Replay-Nonce: D2YrrsmTazwytMqMjoHjqlQ0Hd12w_qfshvV4nuI6ho
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
Expires: Fri, 31 May 2019 09:51:30 GMT
Cache-Control: max-age=0, no-cache, no-store
Pragma: no-cache
Date: Fri, 31 May 2019 09:51:30 GMT
Connection: keep-alive
] Body: *?H???S?&?Al???Dq?5?0?'0
]
DEBUG: get issuer-cert
DEBUG: szUserAgent: [synology_armada38x_ds216j DSM6.2-24922 (DDNS)]
DEBUG: GET Request: https://acme-v01.api.letsencrypt.org/acme/issuer-cert
DEBUG: Curl Reply: [200] Header: [HTTP/1.1 200 OK
Server: nginx
Content-Type: application/pkix-cert
Content-Length: 1174
Replay-Nonce: s4nKwDEsz3MY7SX5koKgdl28aUYaQaNMqUl3X5YIYu0
X-Frame-Options: DENY
Strict-Transport-Security: max-age=604800
Expires: Fri, 31 May 2019 09:51:31 GMT
Cache-Control: max-age=0, no-cache, no-store
Pragma: no-cache
Date: Fri, 31 May 2019 09:51:31 GMT
Connection: keep-alive
] Body: [0??0?z?
AB]
DEBUG: save to files
DEBUG: renew success. [/usr/syno/etc/certificate/_archive/aaaaaa].
********************************** 更新された証明書は、下記の通り
2019年5月31日 17:51:29 JST から
2019年8月29日 17:51:29 JST まで
タイムスタンプが1時間ズレているのは変わらず
----
sh-4.3# openssl x509 -text -noout -in /usr/syno/etc/certificate/_archive/aaaaaa/cert.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
03:26:c9:13:41:6c:f8:b2:b2:44:71:b8:35:b7:12:30:fd:ff
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, O=Let's Encrypt, CN=Let's Encrypt Authority X3
Validity
Not Before: May 31 08:51:29 2019 GMT
Not After : Aug 29 08:51:29 2019 GMT
Subject: CN=XXXXXXXX.YYY.netvolante.jp
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
**:**:........
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
30:D6:80:50:09:DA:AA:15:A8:9B:96:E8:BA:A5:6E:4C:8E:90:33:C4
X509v3 Authority Key Identifier:
keyid:A8:4A:6A:63:04:7D:DD:BA:E6:D1:39:B7:A6:45:65:EF:F3:A8:EC:A1
Authority Information Access:
OCSP - URI:http://ocsp.int-x3.letsencrypt.org
CA Issuers - URI:http://cert.int-x3.letsencrypt.org/
X509v3 Subject Alternative Name:
DNS:XXXXXXXX.YYY.netvolante.jp
X509v3 Certificate Policies:
Policy: 2.23.140.1.2.1
Policy: 1.3.6.1.4.1.44947.1.1.1
CPS: http://cps.letsencrypt.org
CT Precertificate SCTs:
Signed Certificate Timestamp:
Version : v1(0)
Log ID : **:**:........
Timestamp : May 31 09:51:30.147 2019 GMT
Extensions: none
Signature : ecdsa-with-SHA256
**:**:........
Signed Certificate Timestamp:
Version : v1(0)
Log ID : **:**:........
Timestamp : May 31 09:51:30.178 2019 GMT
Extensions: none
Signature : ecdsa-with-SHA256
**:**:........
Signature Algorithm: sha256WithRSAEncryption
**:**:........
----次回の更新は、「2019年7月30日(火) 17:51:29 JST」以降なので、忘れなければ、デバッグ実行して証明書と「new-authz」の有効期限を確認することにする。























朝9時に証明書を更新したのに、ブラウザで証明書を表示させると、8時と表示されます
そんな早くには作業していませんから、驚きました。
「証明書発行時のタイムスタンプが1時間ズレているのが気になる。。。」はなにかその後分かりましたか?
が、コメントで説明が難しいので記事にします。
https://blog.goo.ne.jp/rabbit5151/e/eddbc40f3931f807d52f01fddfe957e0